반응형
1. AWS ALB Ingress 구성
1.1 아키텍처 개요

특징
- ✅ hostNetwork 불필요
- ✅ externalTrafficPolicy 무관 (Service 안 거침)
- ✅ Source IP: X-Forwarded-For 헤더로 전달
1.2 Target Type 비교
IP Mode (기본/권장)
alb.ingress.kubernetes.io/target-type: ipALB → Pod IP 직접
(Service 거치지 않음)
| 항목 | 설명 |
| 트래픽 경로 | ALB → Pod IP 직접 |
| Service 타입 | ClusterIP로 충분 |
| hostNetwork | 불필요 |
| externalTrafficPolicy | 무관 |
| 요구사항 | AWS VPC CNI (Pod가 VPC IP 사용) |
Instance Mode
alb.ingress.kubernetes.io/target-type: instanceALB → Node (NodePort) → kube-proxy → Pod
| 항목 | 설명 |
| 트래픽 경로 | ALB → NodePort → Pod |
| Service 타입 | NodePort 필수 |
| externalTrafficPolicy | Local 설정 시 Source IP 보존 |
| 요구사항 | Security Group에서 NodePort 허용 |
1.3 Service의 역할 (IP Mode)
Service는 필수이지만 트래픽 라우팅에 사용되지 않음:

핵심: 실제 트래픽은 ALB → Pod (Service 거치지 않음)
1.4 ALB Ingress 전체 구성
# 1. Deployment
apiVersion: apps/v1
kind: Deployment
metadata:
name: my-app
namespace: default
spec:
replicas: 3
selector:
matchLabels:
app: my-app
template:
metadata:
labels:
app: my-app
spec:
containers:
- name: app
image: nginx:latest
ports:
- containerPort: 80
resources:
requests:
cpu: 100m
memory: 128Mi
limits:
cpu: 200m
memory: 256Mi
---
# 2. Service (Pod 선택자 역할)
apiVersion: v1
kind: Service
metadata:
name: my-app-svc
namespace: default
spec:
type: ClusterIP # IP mode에서는 ClusterIP로 충분
selector:
app: my-app
ports:
- port: 80
targetPort: 80
protocol: TCP
---
# 3. Ingress (ALB 생성)
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: my-app-ingress
namespace: default
annotations:
# ALB 기본 설정
alb.ingress.kubernetes.io/scheme: internet-facing # 또는 internal
alb.ingress.kubernetes.io/target-type: ip # 권장
# SSL/TLS 설정
alb.ingress.kubernetes.io/listen-ports: '[{"HTTP": 80}, {"HTTPS": 443}]'
alb.ingress.kubernetes.io/certificate-arn: arn:aws:acm:ap-northeast-2:123456789:certificate/xxx
alb.ingress.kubernetes.io/ssl-policy: ELBSecurityPolicy-TLS13-1-2-2021-06
# Health Check 설정
alb.ingress.kubernetes.io/healthcheck-path: /health
alb.ingress.kubernetes.io/healthcheck-interval-seconds: "15"
alb.ingress.kubernetes.io/healthcheck-timeout-seconds: "5"
alb.ingress.kubernetes.io/healthy-threshold-count: "2"
alb.ingress.kubernetes.io/unhealthy-threshold-count: "2"
# 추가 설정
alb.ingress.kubernetes.io/load-balancer-name: my-app-alb
alb.ingress.kubernetes.io/tags: Environment=production,Team=backend
alb.ingress.kubernetes.io/group.name: shared-alb # ALB 공유 시
spec:
ingressClassName: alb
rules:
- host: api.example.com
http:
paths:
- path: /
pathType: Prefix
backend:
service:
name: my-app-svc
port:
number: 80
1.5 주요 Annotations
Scheme (공개/내부)
# Internet-facing (외부 공개)
alb.ingress.kubernetes.io/scheme: internet-facing
# Internal (VPC 내부만)
alb.ingress.kubernetes.io/scheme: internalTarget Type
# IP Mode (권장) - Pod IP 직접
alb.ingress.kubernetes.io/target-type: ip
# Instance Mode - NodePort 경유
alb.ingress.kubernetes.io/target-type: instanceSSL/TLS
alb.ingress.kubernetes.io/listen-ports: '[{"HTTP": 80}, {"HTTPS": 443}]'
alb.ingress.kubernetes.io/certificate-arn: arn:aws:acm:region:account:certificate/cert-id
alb.ingress.kubernetes.io/ssl-policy: ELBSecurityPolicy-TLS13-1-2-2021-06
# ⚠️ HTTP → HTTPS 리다이렉트 (주의: 공유 ALB에서 문제 발생 가능)
# alb.ingress.kubernetes.io/ssl-redirect: "443" # 권장하지 않음Health Check
alb.ingress.kubernetes.io/healthcheck-path: /health
alb.ingress.kubernetes.io/healthcheck-port: traffic-port
alb.ingress.kubernetes.io/healthcheck-protocol: HTTP
alb.ingress.kubernetes.io/healthcheck-interval-seconds: "15"
alb.ingress.kubernetes.io/healthcheck-timeout-seconds: "5"
alb.ingress.kubernetes.io/healthy-threshold-count: "2"
alb.ingress.kubernetes.io/unhealthy-threshold-count: "2"
alb.ingress.kubernetes.io/success-codes: "200-299"ALB 공유 (Group)
# 같은 group.name을 가진 Ingress들은 하나의 ALB 공유
alb.ingress.kubernetes.io/group.name: shared-alb
alb.ingress.kubernetes.io/group.order: "10" # 규칙 우선순위기타
# Idle Timeout
alb.ingress.kubernetes.io/load-balancer-attributes: idle_timeout.timeout_seconds=60
# WAF 연동
alb.ingress.kubernetes.io/wafv2-acl-arn: arn:aws:wafv2:...
# Access Log
alb.ingress.kubernetes.io/load-balancer-attributes: access_logs.s3.enabled=true,access_logs.s3.bucket=my-bucket
# Security Group
alb.ingress.kubernetes.io/security-groups: sg-xxx,sg-yyy
alb.ingress.kubernetes.io/manage-backend-security-group-rules: "true"1.6 Source IP 확인 방법
ALB는 X-Forwarded-For 헤더로 클라이언트 IP 전달:
# Python/Flask
from flask import request
client_ip = request.headers.get('X-Forwarded-For', '').split(',')[0].strip()// Node.js/Express
app.set('trust proxy', true);
const clientIP = req.ip;// Go
clientIP := strings.Split(r.Header.Get("X-Forwarded-For"), ",")[0]2. AWS NLB Service 구성
2.1 아키텍처 개요
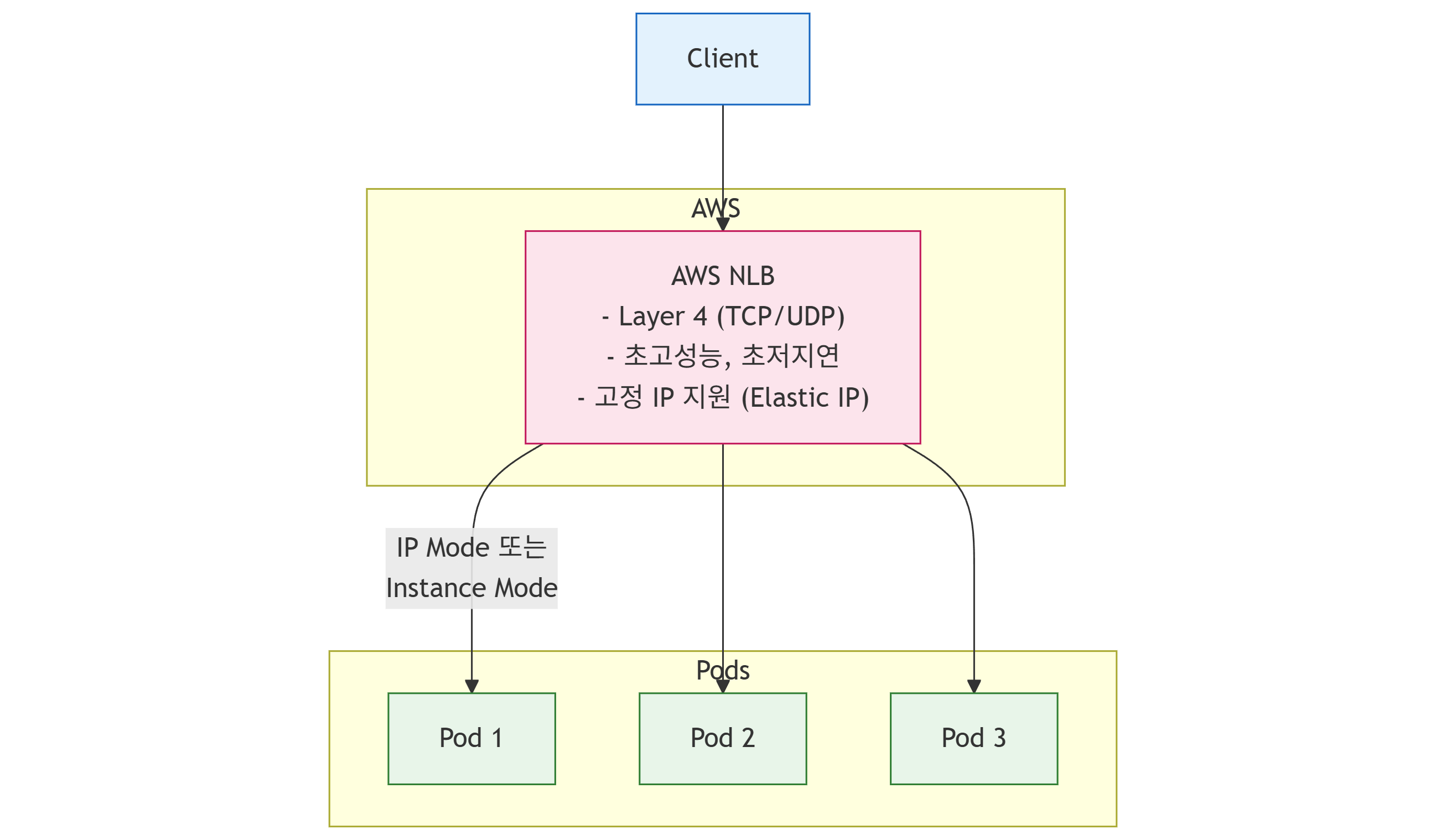
2.2 NLB 기본 구성 (IP Mode)
apiVersion: v1
kind: Service
metadata:
name: my-nlb-service
namespace: default
annotations:
# NLB 타입 지정
service.beta.kubernetes.io/aws-load-balancer-type: external
service.beta.kubernetes.io/aws-load-balancer-nlb-target-type: ip # 권장
# Scheme
service.beta.kubernetes.io/aws-load-balancer-scheme: internet-facing
# 이름 및 태그
service.beta.kubernetes.io/aws-load-balancer-name: my-nlb
service.beta.kubernetes.io/aws-load-balancer-additional-resource-tags: Environment=prod
spec:
type: LoadBalancer
selector:
app: my-app
ports:
- port: 443
targetPort: 8443
protocol: TCP
2.3 NLB Instance Mode (Source IP 보존)
apiVersion: v1
kind: Service
metadata:
name: my-nlb-service
annotations:
service.beta.kubernetes.io/aws-load-balancer-type: external
service.beta.kubernetes.io/aws-load-balancer-nlb-target-type: instance
service.beta.kubernetes.io/aws-load-balancer-scheme: internet-facing
spec:
type: LoadBalancer
externalTrafficPolicy: Local # Source IP 보존
selector:
app: my-app
ports:
- port: 443
targetPort: 8443
protocol: TCP
2.4 NLB + TLS Termination
apiVersion: v1
kind: Service
metadata:
name: my-nlb-tls
annotations:
service.beta.kubernetes.io/aws-load-balancer-type: external
service.beta.kubernetes.io/aws-load-balancer-nlb-target-type: ip
service.beta.kubernetes.io/aws-load-balancer-scheme: internet-facing
# TLS 설정
service.beta.kubernetes.io/aws-load-balancer-ssl-cert: arn:aws:acm:region:account:certificate/cert-id
service.beta.kubernetes.io/aws-load-balancer-ssl-ports: "443"
service.beta.kubernetes.io/aws-load-balancer-ssl-negotiation-policy: ELBSecurityPolicy-TLS13-1-2-2021-06
spec:
type: LoadBalancer
selector:
app: my-app
ports:
- name: https
port: 443
targetPort: 8080 # TLS 종료 후 HTTP로 전달
protocol: TCP
2.5 NLB 고정 IP (Elastic IP)
apiVersion: v1
kind: Service
metadata:
name: my-nlb-eip
annotations:
service.beta.kubernetes.io/aws-load-balancer-type: external
service.beta.kubernetes.io/aws-load-balancer-nlb-target-type: ip
service.beta.kubernetes.io/aws-load-balancer-scheme: internet-facing
# Elastic IP 할당
service.beta.kubernetes.io/aws-load-balancer-eip-allocations: eipalloc-xxx,eipalloc-yyy
spec:
type: LoadBalancer
selector:
app: my-app
ports:
- port: 443
targetPort: 8443
protocol: TCP2.6 NLB Internal (VPC 내부)
apiVersion: v1
kind: Service
metadata:
name: my-internal-nlb
annotations:
service.beta.kubernetes.io/aws-load-balancer-type: external
service.beta.kubernetes.io/aws-load-balancer-nlb-target-type: ip
service.beta.kubernetes.io/aws-load-balancer-scheme: internal
# Private Subnet 지정
service.beta.kubernetes.io/aws-load-balancer-subnets: subnet-xxx,subnet-yyy
spec:
type: LoadBalancer
selector:
app: my-app
ports:
- port: 80
targetPort: 8080
protocol: TCP2.7 NLB 주요 Annotations
기본 설정
# NLB 타입 (필수)
service.beta.kubernetes.io/aws-load-balancer-type: external
# Target Type
service.beta.kubernetes.io/aws-load-balancer-nlb-target-type: ip # 권장
service.beta.kubernetes.io/aws-load-balancer-nlb-target-type: instance
# Scheme
service.beta.kubernetes.io/aws-load-balancer-scheme: internet-facing
service.beta.kubernetes.io/aws-load-balancer-scheme: internalHealth Check
service.beta.kubernetes.io/aws-load-balancer-healthcheck-protocol: HTTP
service.beta.kubernetes.io/aws-load-balancer-healthcheck-port: "8080"
service.beta.kubernetes.io/aws-load-balancer-healthcheck-path: /health
service.beta.kubernetes.io/aws-load-balancer-healthcheck-interval: "10"
service.beta.kubernetes.io/aws-load-balancer-healthcheck-timeout: "5"
service.beta.kubernetes.io/aws-load-balancer-healthcheck-healthy-threshold: "2"
service.beta.kubernetes.io/aws-load-balancer-healthcheck-unhealthy-threshold: "2"네트워크
# Subnet 지정
service.beta.kubernetes.io/aws-load-balancer-subnets: subnet-xxx,subnet-yyy
# Security Group
service.beta.kubernetes.io/aws-load-balancer-security-groups: sg-xxx
# Cross-Zone Load Balancing
service.beta.kubernetes.io/aws-load-balancer-attributes: load_balancing.cross_zone.enabled=true
# Proxy Protocol v2 (Source IP 보존 - Instance Mode)
service.beta.kubernetes.io/aws-load-balancer-proxy-protocol: "*"Access Log
service.beta.kubernetes.io/aws-load-balancer-access-log-enabled: "true"
service.beta.kubernetes.io/aws-load-balancer-access-log-s3-bucket-name: my-bucket
service.beta.kubernetes.io/aws-load-balancer-access-log-s3-bucket-prefix: nlb-logs2.8 NLB Source IP 보존
IP Mode (기본 보존)
# IP Mode에서는 기본적으로 Source IP 보존됨
service.beta.kubernetes.io/aws-load-balancer-nlb-target-type: ipPod에서 직접 클라이언트 IP 확인 가능 (TCP 소켓에서).
Instance Mode + Proxy Protocol
# Instance Mode에서 Source IP 보존하려면 Proxy Protocol 필요
service.beta.kubernetes.io/aws-load-balancer-nlb-target-type: instance
service.beta.kubernetes.io/aws-load-balancer-proxy-protocol: "*"
⚠️ 애플리케이션이 Proxy Protocol v2를 지원해야 함.
3. ALB vs NLB 비교
3.1 기본 비교
| 항목 | ALB | NLB |
| OSI 계층 | Layer 7 (HTTP/HTTPS) | Layer 4 (TCP/UDP/TLS) |
| 프로토콜 | HTTP, HTTPS, gRPC | TCP, UDP, TLS |
| 라우팅 | Host/Path 기반 | 포트 기반 |
| 성능 | 높음 | 매우 높음 (초저지연) |
| 고정 IP | ❌ (DNS만) | ✅ (Elastic IP 지원) |
| WebSocket | ✅ | ✅ |
| SSL 종료 | ✅ | ✅ |
| HTTP 헤더 접근 | ✅ | ❌ |
3.2 Kubernetes 구성 비교
| 항목 | ALB | NLB |
| K8s 리소스 | Ingress | Service (type: LoadBalancer) |
| Controller | AWS Load Balancer Controller | AWS Load Balancer Controller |
| Target Type | ip (권장), instance | ip (권장), instance |
| hostNetwork | 불필요 | 불필요 |
| externalTrafficPolicy | IP mode: 무관 | IP mode: 무관 |
| Source IP | X-Forwarded-For 헤더 | 직접 보존 (IP mode) |
3.3 사용 사례
| 사용 사례 | 권장 |
| HTTP/HTTPS API | ALB |
| 마이크로서비스 라우팅 | ALB |
| gRPC 서비스 | ALB |
| WebSocket | ALB 또는 NLB |
| TCP/UDP 서비스 | NLB |
| 게임 서버 | NLB |
| IoT (MQTT) | NLB |
| 고정 IP 필요 | NLB |
| 초저지연 필요 | NLB |
| VPN/프록시 | NLB |
3.4 트래픽 흐름 비교
ALB (IP Mode)

Source IP: X-Forwarded-For 헤더로 전달
NLB (IP Mode)

Source IP: 직접 보존 (TCP 소켓에서 확인 가능)
4. 실전 구성 예시
4.1 웹 애플리케이션 (ALB)
# Frontend + Backend 분리 구성
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: web-app-ingress
annotations:
alb.ingress.kubernetes.io/scheme: internet-facing
alb.ingress.kubernetes.io/target-type: ip
alb.ingress.kubernetes.io/listen-ports: '[{"HTTP": 80}, {"HTTPS": 443}]'
alb.ingress.kubernetes.io/certificate-arn: arn:aws:acm:...
alb.ingress.kubernetes.io/group.name: web-alb
spec:
ingressClassName: alb
rules:
# Frontend
- host: www.example.com
http:
paths:
- path: /
pathType: Prefix
backend:
service:
name: frontend-svc
port:
number: 80
# API Backend
- host: api.example.com
http:
paths:
- path: /v1
pathType: Prefix
backend:
service:
name: api-v1-svc
port:
number: 80
- path: /v2
pathType: Prefix
backend:
service:
name: api-v2-svc
port:
number: 80
4.2 gRPC 서비스 (ALB)
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: grpc-ingress
annotations:
alb.ingress.kubernetes.io/scheme: internet-facing
alb.ingress.kubernetes.io/target-type: ip
alb.ingress.kubernetes.io/listen-ports: '[{"HTTPS": 443}]'
alb.ingress.kubernetes.io/certificate-arn: arn:aws:acm:...
alb.ingress.kubernetes.io/backend-protocol-version: GRPC
alb.ingress.kubernetes.io/healthcheck-protocol: HTTP
alb.ingress.kubernetes.io/healthcheck-path: /grpc.health.v1.Health/Check
spec:
ingressClassName: alb
rules:
- host: grpc.example.com
http:
paths:
- path: /
pathType: Prefix
backend:
service:
name: grpc-svc
port:
number: 50051
4.3 TCP 서비스 (NLB)
# Redis, Database 등 TCP 서비스
apiVersion: v1
kind: Service
metadata:
name: redis-nlb
annotations:
service.beta.kubernetes.io/aws-load-balancer-type: external
service.beta.kubernetes.io/aws-load-balancer-nlb-target-type: ip
service.beta.kubernetes.io/aws-load-balancer-scheme: internal
spec:
type: LoadBalancer
selector:
app: redis
ports:
- port: 6379
targetPort: 6379
protocol: TCP
4.4 고정 IP 필요 서비스 (NLB + EIP)
# 외부 연동 시 IP 화이트리스트가 필요한 경우
apiVersion: v1
kind: Service
metadata:
name: external-api
annotations:
service.beta.kubernetes.io/aws-load-balancer-type: external
service.beta.kubernetes.io/aws-load-balancer-nlb-target-type: ip
service.beta.kubernetes.io/aws-load-balancer-scheme: internet-facing
service.beta.kubernetes.io/aws-load-balancer-eip-allocations: eipalloc-xxx,eipalloc-yyy
spec:
type: LoadBalancer
selector:
app: external-api
ports:
- port: 443
targetPort: 8443
protocol: TCP
4.5 Internal 서비스 (ALB + NLB 혼합)
# Internal ALB - HTTP 서비스
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: internal-api
annotations:
alb.ingress.kubernetes.io/scheme: internal
alb.ingress.kubernetes.io/target-type: ip
spec:
ingressClassName: alb
rules:
- host: internal-api.corp.local
http:
paths:
- path: /
pathType: Prefix
backend:
service:
name: internal-api-svc
port:
number: 80
---
# Internal NLB - TCP 서비스
apiVersion: v1
kind: Service
metadata:
name: internal-db
annotations:
service.beta.kubernetes.io/aws-load-balancer-type: external
service.beta.kubernetes.io/aws-load-balancer-nlb-target-type: ip
service.beta.kubernetes.io/aws-load-balancer-scheme: internal
spec:
type: LoadBalancer
selector:
app: database
ports:
- port: 5432
targetPort: 5432
protocol: TCP
4.6 다중 포트 NLB (게임 서버)
apiVersion: v1
kind: Service
metadata:
name: game-server
annotations:
service.beta.kubernetes.io/aws-load-balancer-type: external
service.beta.kubernetes.io/aws-load-balancer-nlb-target-type: ip
service.beta.kubernetes.io/aws-load-balancer-scheme: internet-facing
service.beta.kubernetes.io/aws-load-balancer-eip-allocations: eipalloc-xxx
spec:
type: LoadBalancer
selector:
app: game-server
ports:
- name: tcp-game
port: 7777
targetPort: 7777
protocol: TCP
- name: udp-voice
port: 7778
targetPort: 7778
protocol: UDP
5. 요약
5.1 hostNetwork & externalTrafficPolicy 필요 여부
| 구성 | hostNetwork | externalTrafficPolicy |
| ALB + IP mode | ❌ 불필요 | ❌ 무관 |
| ALB + Instance mode | ❌ 불필요 | Local (Source IP 보존 시) |
| NLB + IP mode | ❌ 불필요 | ❌ 무관 |
| NLB + Instance mode | ❌ 불필요 | Local (Source IP 보존 시) |
5.2 Source IP 보존 방법
| LB 타입 | Target Type | Source IP 확인 방법 |
| ALB | IP | X-Forwarded-For 헤더 |
| ALB | Instance + Local | X-Forwarded-For 헤더 |
| NLB | IP | 직접 보존 (TCP 소켓에서) |
| NLB | Instance + Proxy Protocol | Proxy Protocol 파싱 |
5.3 권장 구성
| 요구사항 | 권장 구성 |
| HTTP/HTTPS API | ALB + IP mode |
| 마이크로서비스 | ALB + IP mode + group.name (ALB 공유) |
| gRPC | ALB + IP mode + GRPC backend protocol |
| TCP/UDP 서비스 | NLB + IP mode |
| 고정 IP 필요 | NLB + EIP |
| 초저지연 | NLB + IP mode |
| 복잡한 라우팅 | ALB (Host/Path 기반) |
5.4 Annotations Quick Reference
ALB 필수
alb.ingress.kubernetes.io/scheme: internet-facing | internal
alb.ingress.kubernetes.io/target-type: ip
alb.ingress.kubernetes.io/listen-ports: '[{"HTTP": 80}, {"HTTPS": 443}]'
alb.ingress.kubernetes.io/certificate-arn: arn:aws:acm:...NLB 필수
service.beta.kubernetes.io/aws-load-balancer-type: external
service.beta.kubernetes.io/aws-load-balancer-nlb-target-type: ip
service.beta.kubernetes.io/aws-load-balancer-scheme: internet-facing | internal반응형
'K8S' 카테고리의 다른 글
| Kubernetes hostNetwork & externalTrafficPolicy - AWS ALB, NLB 에서 사용하는가? (0) | 2026.01.26 |
|---|---|
| Kubernetes Windows 지원: 기능 비교와 스케줄링 방식 정리 (0) | 2026.01.23 |
| 쿠버네티스 캐스케이딩 삭제(Cascading Deletion) (0) | 2026.01.22 |
| Kubernetes는 가상화 도구인가? (0) | 2026.01.22 |
| Kubernetes에서 Stateful 앱에 Blue-Green 배포를 적용할 수 있을까? (0) | 2026.01.19 |
댓글